You know by now – this week, it’s about Cyber Security. There’s a lot of material out there on Cyber Security. The only difference here is: we have embedded our working experience with our customers – Current State Review & Way Forward Definition and Implementation of Maturity Levels.
Insurance companies have long been vulnerable to cyber security threats – with the data that they house, their websites, digitalization through web portals/mobile apps etc. As with anything else, pandemic has raised the threat level, significantly high, and continues so, even with pandemic coming to an end (hopefully) & hybrid work model becoming the norm.
Mind you, when we say vulnerability, we are not even talking about the recent Log4shell or past WannaCry cyber-attacks, but about the much more common (/basic) vulnerabilities that we might not even recognize them to be and leave them unaddressed.
Let’s start with those basic vulnerabilities – Do you connect with any or all the following? And you know, the exposures we are subject to
- Company website vulnerability for phishing & malware attacks – when you open a website that’s been compromised, there can be a malware that can get downloaded onto your laptop
- Our Emails & passwords – we all have that one favourite password which we use for any/all our logins (after all how many can we remember right??). Once an email account is breached, the email/password combination can be run through any of the ecommerce websites. For example, one successful login into our amazon account – rest is history. That’s why our IT teams force a password reset once a month or two/asks for enabling an MFA 😊, right?
- Our work desks – Not maintaining a clean desk policy. For the things that we do not remember, we generally write somewhere. Sometimes, it can be our work desks, with system access passwords
- The list continues….
If something as simple as the above can open up ourselves to the external world, difficult to understand the totality of exposure, around the information & the downstream damages.
If you have not already done, it may be a good idea to ask a question internally, where are we, on the cyber security, now and what measures do we have in place, to ensure we are cyber resilient continuously?
Some insights for you, while you await internal response.
As per the NIST – 800 security standards framework (a catalog of security and privacy controls defined by National Institute of Standards and Technology), an organization for it to be cyber re-silent needs to consider the following key protocols,
- Identify – Develop organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities. Categories include – Asset Management, Business Environment, Governance, Risk assessment & management strategy
- Protect – Develop & implement the appropriate safeguards to ensure delivery of critical infrastructure services. Categories include – Access Control, Awareness & Training, Data security, Information Protection, Maintenance & Protective Technology
- Detect – Develop & implement appropriate activities to identify the occurrence of a cybersecurity event. Categories include – Anomalies & Events, Security Continuous Monitoring and Detection processes
- Respond – Develop & implement the appropriate activities to take action regarding a detected cybersecurity event. Categories include – Response planning, Communications, Analysis, Mitigation, and Improvements
- Recover – Develop & implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event. Categories include – Recovery planning, improvements & communication
Maturity Framework as against the security protocols, explained at a very high level
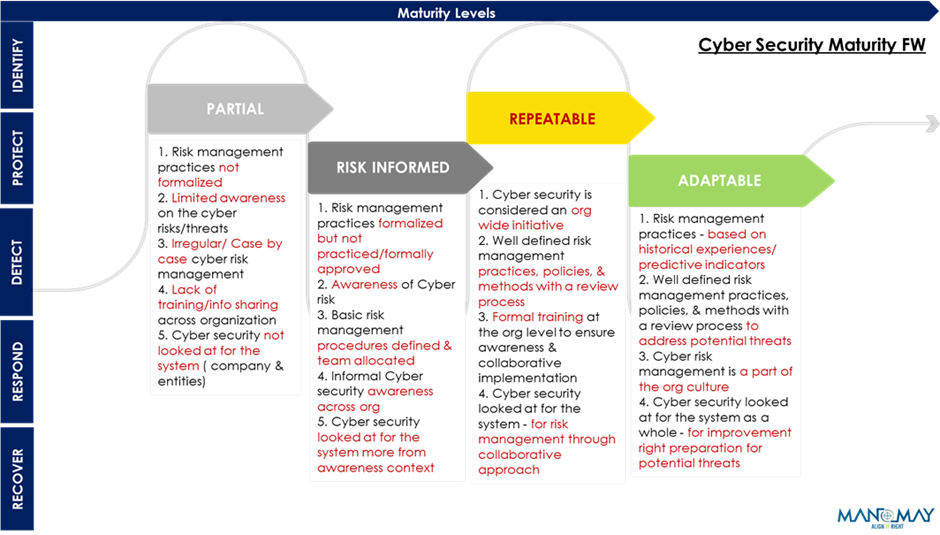
** Security Protocols & Maturity Levels defined are as per the NIST 800 FW, re-phrased/modified by Manomay to be suitable for insurance companies
The security protocols and maturity levels that need to be considered vary by the industry/type of the company. For Insurance companies, the recommended basic maturity level is to be at ‘Repeatable’.
Map the response to the framework above and you know where you are & your preparedness & readiness for future.
A little tidbit on the review/assessment of your current maturity,
- Areas of assessment – Applications, Users, Network, Data, Middleware (Databases, APIs etc.), Operating systems, Hardware/Devices etc.
- Process of assessment – Posture assessment, Security testing, Vulnerability Assessment & Penetration Testing (VAPT) etc.
Cyber resilience is an Org Standardization/Maturity initiative, a BCP of a kind that also warrants a culture shift. One step at a time and continuing with the steps, with course corrections – continue with the journey!
Reach out to us for a deep dive (we just focused on basics for CXOs) or in case of inquiries at inquisite@manomay.biz / biztechinsights@manomay.biz
“Every case involving cybercrime that I’ve been involved in, I’ve never found a master criminal sitting somewhere in Russia or Hongkong or Beijing. It always ends up that somebody at the company did something they weren’t supposed to do. They read an email, or went to a website they weren’t supposed to” – Frank Abagnale
Biz Tech Insights Team Manomay
Disclaimer: The views and findings expressed in this material are for informational and educational purposes only. It is not intended as a guideline, recommendation or a substitute to any form of Professional (Consulting or Technology) advice. Under no circumstance shall we bear a legal responsibility for the use or reliance of any information mentioned in this article.Unless otherwise specified, the views, case studies and findings expressed herein are our own. The content displayed here is the Intellectual Property of Manomay Consultancy Services (India) Pvt Ltd. You may not reuse, republish or reprint any of the aforementioned content without our written consent.

